SCRM Problem
The SCRM problem arises from both introduced vulnerabilities and external threats to a system or its components. Taken together they comprise the primary risk to the ICT SCRM supply chain.
Threats and Vulnerabilities
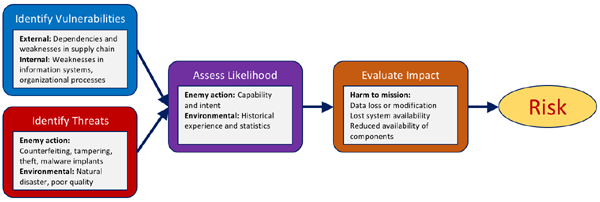
Within the ICT SCRM supply chain, a weakness creates a vulnerability that can be exploited or triggered by a threat or attack on the supply chain. Weaknesses, threats to/attacks on, the supply chain compromise the integrity, security, confidence in and reliability of, the supply chain. Weaknesses and threats at any point in the supply chain (system/component design, manufacturing, shipping, delivery, operation and end-of-life) are created and implemented by bad actors (individuals, organizations, or nation states). These risks (vulnerabilities and threats) are difficult to detect, hi-tech and complex. They are a considerable risk to organizational reputation, operations, image, assets and capabilities.
Vulnerabilities in the ICT supply chain include both potential exposures to external threat actions including counterfeit parts, tampering with manufactured parts, production of unauthorized or inferior parts, theft and resale of parts, recycled parts, insertion of malicious software, and firmware containing bad parts and/or software. They also include intrinsic exposures to environmental factors such as natural disaster, manufacturing quality, weather, strikes, or single points of failure. Recently a potential vulnerability emerged with the increase in US tariffs placed on China. China's advanced mining producers have long traded with the US in rare metals and minerals vital to ICT technology. There is concern that, in retaliation to the US tariff increase, China might shut down the flow of these basic raw materials essential to future technology and weapons systems. The US, with limited reserves and the ability to quickly build domestic or switch to new foreign sources, would find it difficult to recover. Suggested solutions to most of these vulnerabilities can be found in the section on SCRM Solutions.
Threats to the ICT supply chain include enemy actions and environmental conditions. Threats are countered by the practice of high-quality and effective Supply Chain Risk Management and Mitigation techniques, processes and policies. Information related to these topics can be found in our section onSupply Chain Management, Risk Mitigation And Governance.
Vulnerability and Threat risks are increasing and associated with an organizations decreasing visibility of the supply chain and the processes, procedures, and practices used to deliver the products and services to the customer. It is impossible to eliminate all risks or guarantee all customer products. But it is possible to take advantage of the standards and best practices, and consistently measure and manage the ICT supply chain.