Processes
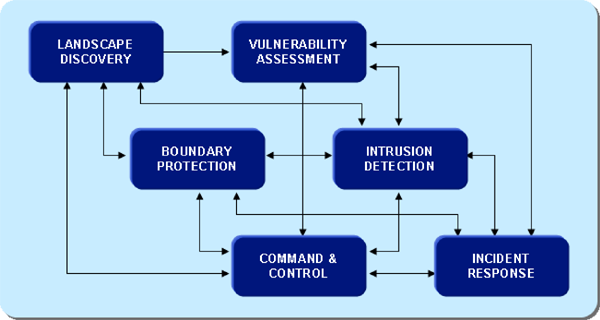
This section provides a generic functional discussion of the common processes in cyber operations. These same processes are present in some way, with the specifics tailored depending on the mission, organization, and systems. These processes take one context for a defensive operation (such as CND) and a different context for an offensive operation (including CNE and CNA).
Landscape Discovery

The information landscape forms the battlespace for the cyber operations. Through the Landscape Discovery process, situational awareness is developed of the active information environment. This discovery process is conducted through a combination of information gathering activities including: observation, measurement, and detection of the information systems. Through this process, the following knowledge is discovered: the types of information hosted on these systems, its sensitivity, the users of these systems, the internal and external communication links, information system boundaries, and boundary controls. Landscape discovery can be conducted by combinations of methods including interviews, automated or manual probing, scanning, and assessment of boundary systems, networks, servers, protocols, user devices, and protective systems.
Boundary Protection
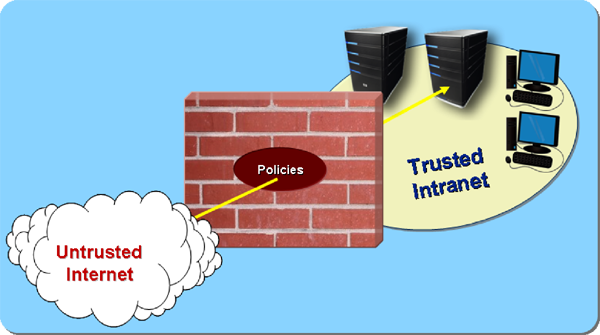
The boundary protection process includes working with the firewalls and other boundary protection systems controlling the boundary network connections between security zones. Firewalls connect two or more networks, typically untrusted networks and trusted networks. They provide access control and accountability at these interfaces to provide the fundamental cyber security services of confidentiality, integrity, and availability. In defensive cyber operations, the boundary protection process includes defining, implementing, and monitoring security policies configured on the firewalls. For offensive operations, this involves probing the boundaries for openings that can be exploited. Although it is convenient to think of firewalls as routing filters that permit or deny specific types of network traffic, they actually provide much more robust boundary protection, and their presence requires special attention in both defensive and offensive cyber operations. In addition to their filtering policies, firewalls also provide proxied routing, split domain name service, and network translation services. The boundary protection service conceals the trusted networks from the untrusted networks, except for specific servers and services that are enabled in the firewalls to allow external name resolution and proxied routing on specified services (or ports) such as for web servers.
In offensive cyber operations, firewalls require special attention since they interfere with access to the information and services on the internal network. Activities to circumvent firewalls include tunneling and bridging. Tunneling includes techniques to encapsulate activities that are not permitted by the firewall within activities that are allowed. An example of this is the use of the web (http) communications protocol which is typically permitted through firewalls to tunnel covert communications for command and control or for exfiltration (i.e., extraction) of collected information. Bridging includes techniques to bypass the firewall through the use of unintended communication paths. A simple example of bridging is the use of a dial-up modem on an internal desktop computer to create a backdoor into a protected network.
Vulnerability Assessment
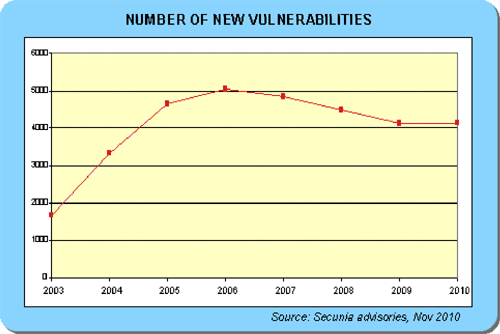
The vulnerability assessment process involves measuring and tabulating the vulnerabilities of the systems identified during the landscape discovery process. These vulnerabilities have their roots in commercial information technology (IT) products that are inherently insecure. Despite ongoing initiatives by product vendors, IT security is far from a solved problem; with new vulnerabilities being discovered constantly, at an average rate of 400 new vulnerabilities a month. These vulnerabilities expose the affected products to a large variety of compromises including confidentiality / privilege violations, Integrity / corruption, availability / denial of service, non-repudiation / accountability. The scale and variety of these vulnerabilities results in an environment that can never be completely protected, resulting in challenges for defensive cyber operations and opportunities for offensive operations.
Intrusion Detection
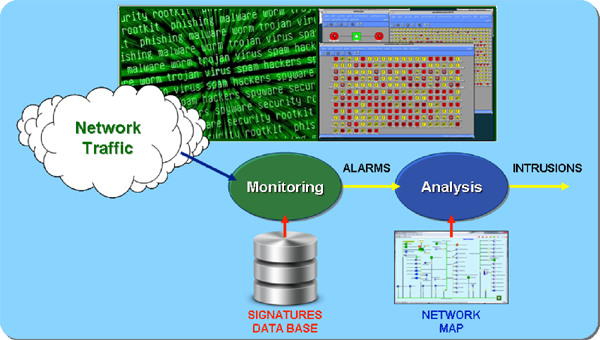
The Intrusion detection process includes inspecting network and host activities to detect intrusions and security relevant events, provide notifications, log and protect relevant information for analysis and investigation. The conventional method of conducting intrusion detection is to iteratively capture samples of network traffic and correlate it against stored data bases of exploit signatures. When traffic matches previously known signatures, alarms are generated for analysis against other information including the network maps generated by the landscape discovery process and the vulnerability assessments. The results of this process are the confirmed intrusions and the recommended responses.
Within defensive cyber operations, there are many challenges including effectively detecting advanced network exploits and maintaining the currency of the systems signature data base. Some threats pose unique challenges, such as new ("day zero") attacks. An important element of intrusion detection is the ability to attribute the observed attack sources to the associated adversaries. A successful intrusion detection process also includes communicating current security status information to assist in managing responses and controlling the enterprise security posture through vulnerability reductions and improved boundary protection.
While conducting offensive cyber operations within an adversary's infrastructure, the goal is to detect the presence of other users whose presence may interfere with mission tasks and to evade detection by the adversary or his intrusion detection systems. This typically involves using stealthy methods of communications, passive or limited methods of probing the host and network infrastructures to minimize the probability of detection. Additionally, the tools that might be deployed may be limited to open-source components that would not be easily attributed to the source.
Incident Response
The incident response process includes both the initial actions taken to correct and manage the immediate incident, and the subsequent corrective actions to address the root-cause of the problem that enabled the incident.
For defense cyber operations, the initial response is usually to block the successful intrusion, to remove any remaining presence on the defended information infrastructure, and repair any damage done by the adversary. In some special cases, where there is interest in additional information about the threat, the intrusion may be permitted to continue some portion of its activities to allow them to be studied or traced to their perpetrator. The subsequent corrective actions are to patch or otherwise remove any detected vulnerabilities in the targeted systems, and to tighten the security posture of the boundary protection systems to provide enhanced blocking of the detected activity. If appropriate, improved business processes and user training may be implemented. The intended result is an improved security posture for the defended infrastructure.
For offensive cyber operations, the scenario and considerations are reversed. The goal is to avoid detection and response by the adversary. Some of this is done through a risk analysis as part of the mission planning. But there is no assurance that activities will go undetected, so continued vigilance is needed to look for indications that the mission might be compromised. Depending on sensitivity, some missions may include provisions for abort, removal, obfuscation or non-attribution. Abort is simply the termination of the offensive operation. Removal involves the use of anti-tampering technologies to prevent the exploits being used from being captured and re-used (or "turned") by the adversary against our national interests. Obfuscation includes a combination of methods designed to conceal or misdirect attempts by the adversary to reverse-engineer any captured remnants of the technology being employed by the adversary. Non-attribution is the use of open-source or other components that are not unique to our capabilities that would provide the adversary with artifacts that would compromise sources and methods.
Command and Control
Any managed operation requires effective command and control. This requires communications methods that are reliable and secure.
For defensive cyber operations, the command and control provides visibility and control of security policies, including planning, implementation, verification, and reporting of system status and security events. This security management communications is normally conducted in separate out-of-band channels from those used by the systems being protected.
For offensive cyber operations, command and control communications also need to be secure, but providing this outside of controlled infrastructures such as within an adversary's network is a greater challenge. Considerations include the need for low detectability, confidentiality, and integrity of both the control instructions and for the collected information being returned.