Compliance
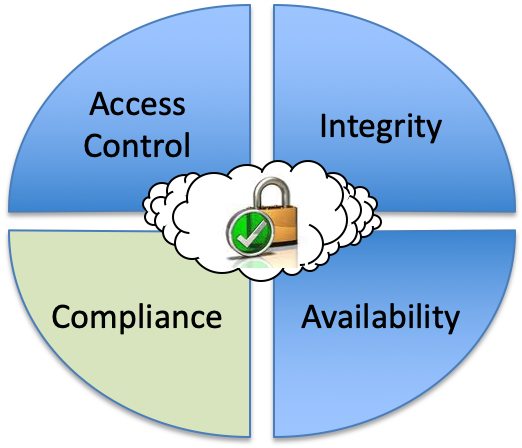
Compliance describes how the user ensures that security objectives are being satisfied in the cloud just as well as they would have been in a conventional IT environment.
As a user moves data from conventional systems to the cloud it remains their responsibility to ensure they remain compliant to all applicable laws, industry standards and regulations. While cloud providers and compliance consultants can offer tools and assistance, the final responsibility and non-compliance consequences remain with the user, not the cloud provider.
Governance is the foundation and starting point for the compliance process. Just as a conventional IT governance framework touches every facet of a business and the people. A cloud governance security framework is no different and must allow the user to view, assess and manage all: identity, credential, and privileged user system access issues (addressed in detail in the Access and Integrity Pages); and risk, security, and compliance issues. A governance framework might also include: a) Highlighting employee security awareness, especially the effect a security breach would have on their organization and potentially others in the cloud environment; b) create a horizontal audit compliance framework that provides a view across all business units and combines the respective information streams to show where the business is vulnerable across the board, rather than only in disparate silos; c) Implement a log management tool which combines security incident and security event management to ensure a complete view of the organizations security posture and integrates the organizations identity and access management solution; and d) manage the inevitable effect of organizational change, a Critical Success Factor (CSF) in a cloud computing transformation, by being prepared to answer questions - i.e. will certain existing roles and resources continue to be necessary, does the organization have the right skills available, can the organization continue to drive the ongoing transition to the cloud, and many more.
A cloud security audit ensures that the user abides by compliance issues that are at risk and are identified and remediated. In a cloud environment the most difficult issue a user faces is providing proof to the audit examiner that compliance issues are not only identified but constantly monitored, immediately identified if at risk, and secured. A sample list of areas considered auditable would contain, but not limited to: Data protection, Incident response, Logs and audit trails, Availability, Identity management, etc.
An Intrusion Detection System (IDS) can be hardware or software that monitors networks or applications for malicious activity, typically malware or viruses. When malicious activity is detected, actionable information should be generated and reported to a central administrator using a security information and event management system (SIEM). Multiple source information is combined by the SIEM to differentiate between genuine and false alarms. This process should be familiar in a conventional IT environment using network monitors and software such as Norton and MacAfee. In the cloud, the provider normally offers 3 types of services: Software as a Service (SaaS) in which the user has little ability to participate in the monitoring or intrusion detection (ID) process; Platform as a Service (PaaS) where the user has more leeway to configure applications and platforms to generate centralized logs that can be used for monitoring, alerting and IDS action; and Infrastructure as a Service (IaaS) which, while placing a larger cost and effort burden on the user, provides the most options to deploy ID in certain locations that feed into your IDS. The responsible users configuration of the cloud IaaS should ensure IDS in the virtual machine (VM); in the host system monitoring both the host and data to and from the VMs; in the virtual network; and the traditional network. Additionally, cloud provider service-level agreements (SLAs) should require immediate user notification of attacks and the user cloud-deployed ID should integrate with local monitoring and alerting systems. Security Analytics is tied closely to the discussion of Metrics in the Integrity Page and the Intrusion Detection System paragraph above. But the recommended ID security protection can interfere with application and network performance. Cloud performance issues are often expressed as overall availability, which is tied to factors (such as excessive encryption), that can result in network latency, and sluggish application implementation. Monitoring application workflow in the cloud is a key user responsibility to ensure positive end-user experience.